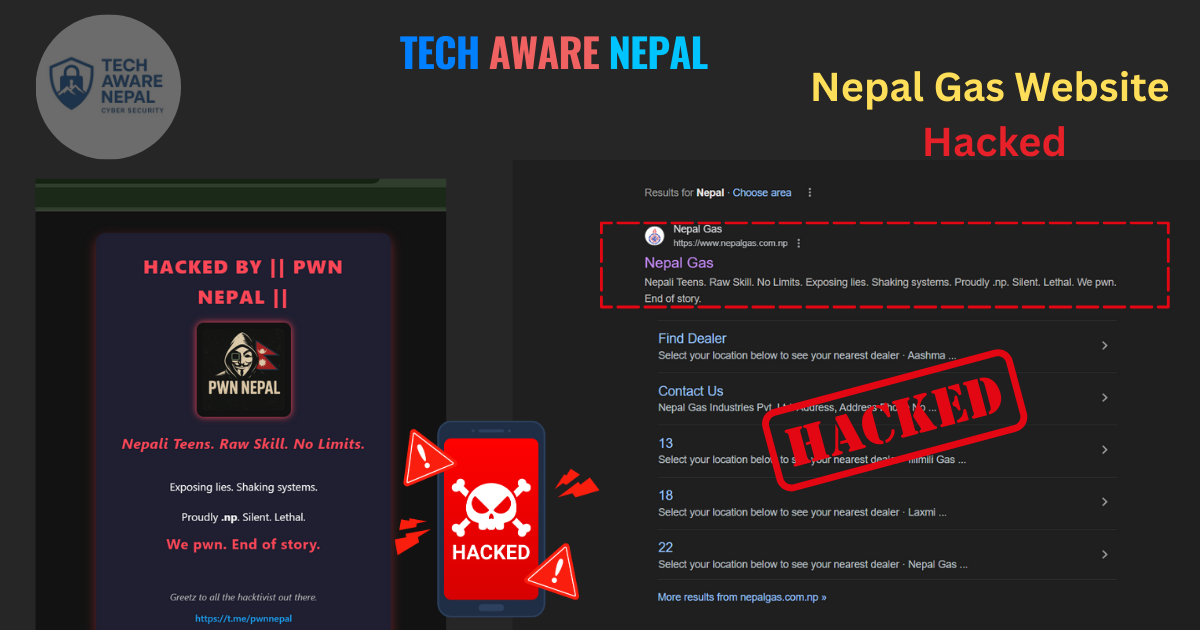
Nepal Gas Website Hacked by PWNNEPAL
On July 09, 2025, , the Nepal Gas website was compromised by the hacking group PWNNEPAL, which claimed to have used Remote Code Execution (RCE) and Reflected Cross-Site Scripting (RXSS) to execute the breach.
Incident Details
The attackers, identifying themselves as “Nepali Teens” with “Raw Skill. No Limits,” likely exploited RCE to execute arbitrary code on the server, possibly through unpatched vulnerabilities or misconfigured settings. RXSS was employed to inject malicious scripts, reflected through the website’s responses, resulting in the defacement with “HACKED” messages and group branding.
Potential Methods
RCE may have provided initial server access, allowing administrative control, while RXSS facilitated the defacement by exploiting unsanitized input fields or manipulated URLs. The group’s “Silent. Lethal” moniker suggests a stealthy, advanced approach, potentially involving zero-day exploits or sophisticated payloads.
Remediation Steps
- Immediate Action: Take the website offline to halt further exploitation.
- Investigation: Conduct a thorough analysis to identify exploited vulnerabilities, such as unpatched software or input handling flaws.
- Restoration: Restore systems from secure, verified backups.
- Patching: Apply security updates to eliminate RCE vulnerabilities.
- Input Security: Implement input validation and output encoding to mitigate RXSS risks.
- Enhanced Security: Deploy multi-factor authentication and a Web Application Firewall (WAF).
Long-Term Prevention
- Conduct regular security audits and penetration testing.
- Provide employee training on cybersecurity best practices.
- Implement continuous monitoring with intrusion detection systems.
Conclusion
The Nepal Gas hack, executed through RCE and RXSS, underscores the evolving cyber threats faced by organizations. Implementing the outlined remediation and prevention strategies is critical to restoring and securing the website against future attacks.