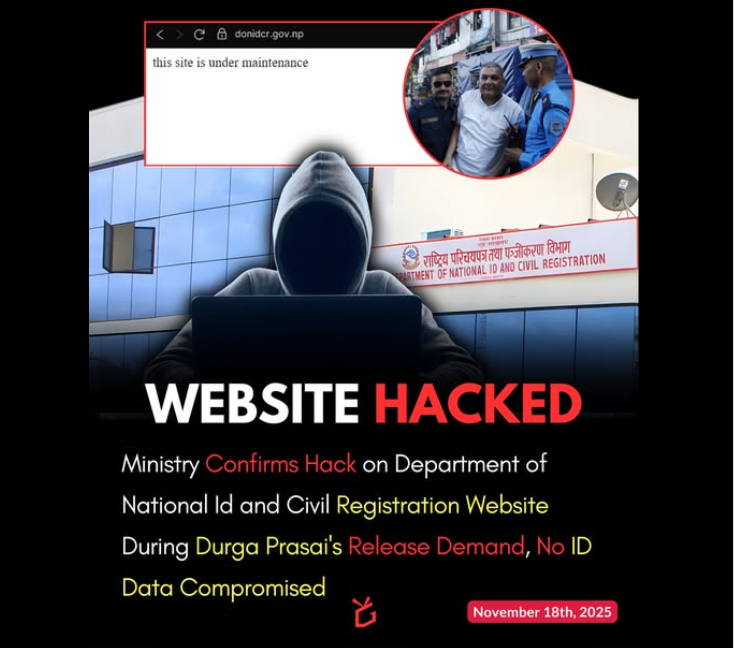
Warning about FreePBX zero-day exploit with CVSS 10.0 critical flaw.
Butwal, Nepal – August 29, 2025
By Tech Aware Nepal Editorial Team
A critical zero-day vulnerability in FreePBX, a widely used open-source Private Branch Exchange (PBX) platform, has been actively exploited since August 21, 2025, posing severe risks to businesses and organizations in Nepal and worldwide. The flaw, rated a maximum CVSS score of 10.0, affects systems with the Administrator Control Panel (ACP) exposed to the public internet, particularly those using the commercial Endpoint Manager module. This article outlines the vulnerability, its impact, and urgent steps for mitigation, tailored for Nepal’s tech community.
Understanding the FreePBX Zero-Day Vulnerability
FreePBX, built on the Asterisk platform, is a cornerstone for managing voice communications, extensions, SIP trunks, and call routing in businesses, call centers, and service providers across Nepal. The zero-day flaw, identified in the commercial Endpoint Manager module, allows unauthenticated attackers to escalate privileges and execute remote code (RCE) on affected systems. This vulnerability enables threat actors to gain full control over the PBX system, manipulate configurations, divert calls, compromise SIP trunks, and potentially generate unauthorized international traffic, which could lead to significant financial losses.
The Sangoma FreePBX Security Team issued an emergency advisory on August 26, 2025, confirming that the exploit has been actively abused since August 21. Compromised systems have exhibited erratic behavior, unauthorized configuration changes, and the presence of malicious scripts, such as .clean.sh in /var/www/html. Reports from affected users indicate widespread breaches, with one organization noting that 3,000 SIP extensions and 500 trunks were compromised.
Impact on Nepal’s Businesses and Organizations
In Nepal, where FreePBX is popular among small and medium-sized enterprises (SMEs), call centers, and IT service providers, the vulnerability poses a significant threat. Many organizations rely on FreePBX for cost-effective communication solutions, but the exposure of the Administrator Control Panel to the internet—often due to misconfigurations or lack of awareness heightens the risk. Attackers exploiting this flaw could disrupt operations, steal sensitive call data, or incur substantial costs through unauthorized international calls, which could be particularly devastating for Nepal’s growing tech ecosystem.
The lack of immediate patches for systems with expired support contracts further complicates the situation for Nepalese businesses, as they may struggle to access the necessary updates. This underscores the importance of proactive cybersecurity measures in a country where digital infrastructure is rapidly expanding but often lacks robust security protocols.
Mitigation Steps for Nepalese Administrators
The Sangoma FreePBX Security Team has released an EDGE fix for new installations, but it does not address already compromised systems. Administrators in Nepal are urged to take immediate action to secure their FreePBX deployments. Below are the recommended steps:
- Restrict Internet Access to the Administrator Control Panel:
- Immediately block public access to ports 80 and 443 using firewall rules or the FreePBX Firewall module. Limit access to trusted IP addresses only.
- Example iptables commands for securing the system:
iptables -I INPUT -p tcp --dport 443 -s <trusted_admin_IP> -j ACCEPT iptables -I INPUT -p tcp --dport 443 -j DROP iptables -I INPUT -p tcp --dport 80 -j DROP - Alternatively, place the PBX behind a VPN or an isolated management VLAN to minimize exposure.
- Apply Available Updates:
- For FreePBX version 16, run the command:
fwconsole ma downloadinstall endpoint --tag 16.0.88.19 - For FreePBX version 17, use:
fwconsole ma downloadinstall endpoint --tag 17.0.2.31 - PBXAct appliances follow the same update commands. Check module versions via the Admin → Module Admin menu once the stable release is available.
- For FreePBX version 16, run the command:
- Check for Indicators of Compromise (IoCs):
- Inspect systems for signs of exploitation, including:
- Presence of the malicious
.clean.shfile in/var/www/html. - Unauthorized changes in
/etc/freepbx.conf. - Suspicious POST requests to
modular.phpin web server logs since August 21. - Unexpected calls to extension 9998 in Asterisk logs.
- Unusual
ampuserentries in MariaDB logs.
- Presence of the malicious
- Use the community-supplied forensic collection script (
collect_forensics_freepbx.sh) to preserve logs and configurations for analysis:./collect_forensics_freepbx.sh --dest /secure/forensics --confirm ```[](https://gbhackers.com/freepbx-servers-hit-by-0-day-exploit/)[](https://cyberpress.org/0-day-exploit-hits-freepbx-servers-admins-warned-to-cut-internet-access/)
- Inspect systems for signs of exploitation, including:
- Restore and Rebuild Systems:
- If compromise is detected, restore systems from backups dated before August 21, 2025, and store them on offline media.
- Deploy a fresh FreePBX instance with updated modules, restore configurations, and rotate all credentials, including SIP trunks and voicemail PINs.
- For organizations without recent backups, perform a temporary cleanup to maintain service, but prioritize a full reinstall.
- Enhance Security Practices:
- Change all administrative credentials and rotate API keys.
- Inspect dialplan configurations and custom scripts for backdoors or injected payloads (e.g., base64-encoded commands or cronjobs invoking
curlto remote servers). - Regularly audit system exposure and ensure no unauthorized modules are active.
Broader Implications for Nepal’s Cybersecurity Landscape
This incident highlights the critical need for robust cybersecurity practices in Nepal’s tech sector. As businesses increasingly adopt VoIP solutions like FreePBX, the exposure of administrative interfaces to the internet remains a common vulnerability. Nepalese organizations must prioritize network segmentation, regular software updates, and employee training to mitigate such risks. The active exploitation of this zero-day flaw serves as a wake-up call for local IT administrators to adopt a proactive stance against cyber threats.
The Sangoma FreePBX Security Team is continuing its investigation and will publish a formal CVE identifier and post-mortem analysis once the vulnerability is fully assessed. In the meantime, Nepalese businesses should stay vigilant, follow Sangoma’s advisories, and engage with local cybersecurity communities for support.
Conclusion
The FreePBX zero-day vulnerability (CVSS 10.0) is a critical threat that demands immediate action from administrators in Nepal and beyond. By restricting internet access, applying updates, and conducting thorough system audits, organizations can mitigate the risk of compromise. Tech Aware Nepal urges all FreePBX users to act swiftly to protect their communication infrastructure and stay informed through trusted sources like the FreePBX Community Forums and Sangoma’s official advisories.
For further updates, follow Tech Aware Nepal on our website and social media channels. Stay safe, and secure your systems today.
References: