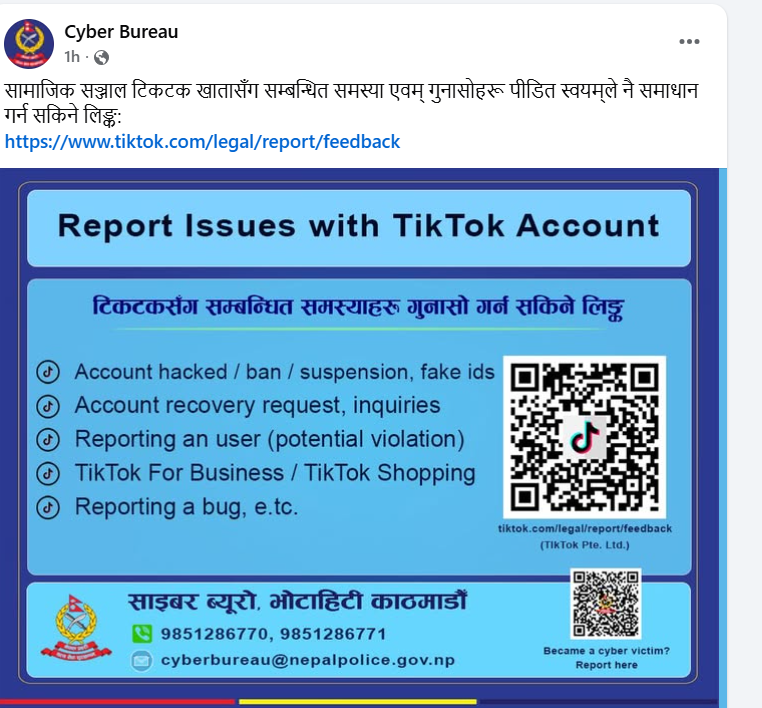
Illustration showing a hacker advertising an Android zero-day exploit on the dark web.
Critical Android Zero-Day Exploit for Versions 11-15 Allegedly for Sale on Dark Web
Introduction
A significant cybersecurity threat has emerged with reports of a critical zero-day exploit targeting Android devices being offered for sale on a cybercrime forum. This vulnerability, which allegedly affects Android versions 11 through 15, poses a severe risk to millions of users globally, as it remains unknown to Google, the developer of the Android operating system, and lacks a security patch.
Details of the Exploit
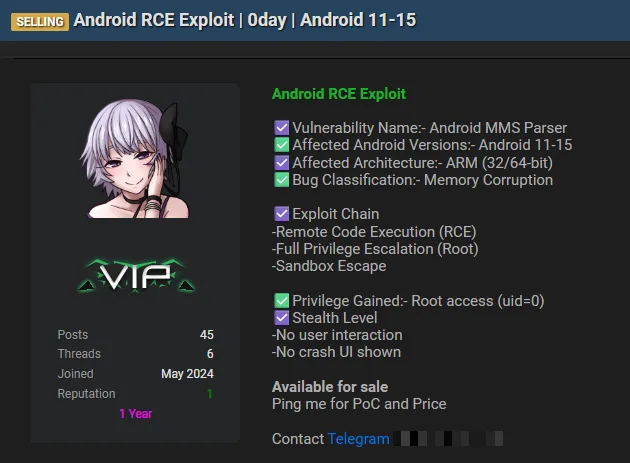
According to a post on a dark web forum, as reported by Daily Dark Web on August 30, 2025, the exploit is a “zero-click” remote code execution (RCE) attack that exploits a memory corruption flaw in the Android MMS Parser. This type of attack is particularly dangerous because it requires no user interaction, such as clicking a malicious link or opening a compromised file, to compromise a device. The exploit reportedly bypasses Android’s robust security mechanisms, including its sandbox, to achieve full root access (uid=0). This level of access grants an attacker complete control over the targeted device, enabling them to execute arbitrary code, access sensitive data, install malware, or perform other malicious activities without the user’s knowledge.
The seller’s claims, as detailed in the forum post, highlight the severity of the vulnerability:
- Vulnerability: Memory Corruption in Android MMS Parser
- Attack Vector: Remote Code Execution (RCE)
- Privilege Gained: Full Root Access (uid=0)
- Stealth: No user interaction required, and no crash notifications displayed
This combination of features makes the exploit exceptionally dangerous, as it allows attackers to compromise devices silently and efficiently. The affected Android versions (11 through 15) encompass a wide range of devices, including smartphones and tablets used by millions of consumers and businesses worldwide.
Potential Impact
The implications of such an exploit are profound. With full root access, an attacker could access personal data, including contacts, messages, photos, and financial information, or use the compromised device for espionage, ransomware deployment, or as part of a botnet for larger cyberattacks. The “zero-click” nature of the exploit heightens the risk, as users may remain unaware of the compromise until significant damage has occurred. Given that Android powers over 2.5 billion active devices globally, the potential scale of this vulnerability is staggering.
The sale of this exploit on the dark web raises additional concerns, as it could be acquired by cybercriminals, state-sponsored actors, or other malicious entities. The absence of a patch from Google leaves affected devices vulnerable until a fix is developed and distributed, a process that could take weeks or longer, depending on the complexity of the vulnerability.
Response and Mitigation
As of now, Google has not publicly acknowledged the vulnerability, consistent with the seller’s claim that it is a zero-day exploit. Cybersecurity experts urge Android users to exercise caution, particularly with MMS messages, and to monitor for any unusual device behavior. While specific mitigation steps are limited without a patch, users are advised to:
- Disable automatic MMS retrieval in messaging apps where possible.
- Keep devices updated with the latest security patches and software updates.
- Install reputable security software to detect and block potential exploits.
- Avoid connecting to unsecured networks, which could facilitate such attacks.
Google is likely to prioritize the investigation and patching of this vulnerability once it becomes aware of the issue. Historically, the company has responded swiftly to critical vulnerabilities, releasing patches through monthly security updates for supported devices. However, older devices running Android versions 11 through 15 may no longer receive updates, leaving them particularly vulnerable.
Broader Context
The discovery of this exploit underscores the ongoing challenges in securing mobile operating systems against increasingly sophisticated threats. Zero-day exploits, particularly those requiring no user interaction, are highly sought after in underground markets due to their effectiveness and stealth. The sale of such exploits on the dark web highlights the lucrative nature of the cybercrime economy, where vulnerabilities can fetch high prices from malicious actors.
This incident also raises questions about the timely detection and disclosure of vulnerabilities. While the exploit’s details remain limited, its presence on a cybercrime forum suggests that it may have been known to certain actors for some time before reaching public awareness. Cybersecurity researchers continue to monitor dark web forums to identify and report such threats, but the window between discovery and patching remains a critical period of risk for users.
The alleged zero-day exploit targeting Android versions 11 through 15 represents a critical threat to the security of millions of devices worldwide. Its “zero-click” nature, combined with the potential for full root access, makes it a powerful tool for attackers. Until Google releases a patch, Android users must remain vigilant and take proactive steps to minimize their exposure. This incident serves as a stark reminder of the importance of timely security updates and robust cybersecurity practices in an era of evolving digital threats.
For further details, refer to the original report by Daily Dark Web: Critical Android Zero-Day Exploit for Versions 11-15 Allegedly for Sale on Dark Web.